Barkly Runtime Malware Defence

Shortly after publishing my previous blog post, I accidentally stumbled upon Barkly. They represent a new breed of security technologies which have departed from traditional signature based detection methods and instead utilise machine learning and behaviour analysis for malware prevention.
At the time, I hadn’t heard of Barkly before. After a quick search online I found no independent reviews or any real exposure within IT communities such as Reddit’s /r/Sysadmin, /r/NetSec or Spiceworks. This needed to change, so I reached out to Barkly for a review copy and they were kind enough to hook me up with a trial.
In this post I’ll be putting Barkly through its paces and seeing how well it performs against a variety of threats, including ransomware, trojans, and exploits.
How does it work?
Barkly is rather unique in that it acts as a last line of defence, attempting to detect and block malware at the time of execution. It is designed to compliment antivirus and work downstream from it, monitoring the runtime behaviour of files and application which have been marked clean and allowed to run.
In order to do this, Barkly has built the ‘Rapidvisor’. A lightweight hypervisor-based agent that has a comprehensive view of user processes, operating system functions, and CPU usage.
The Rapidvisor agent adds a new strategic line of defence to each endpoint, with antivirus software providing pre-execution defence, and Barkly providing post-execution defence.
Because of this approach, Barkly has no ability to scan files or hard-drive’s for malware, however where it should shine is with fileless and in-memory attacks.
Setup and Installation
All management of Barkly is conducted from their online console. Once logged in, I was first greeted with a ‘get started’ screen which makes deployment to devices super simple and fast.
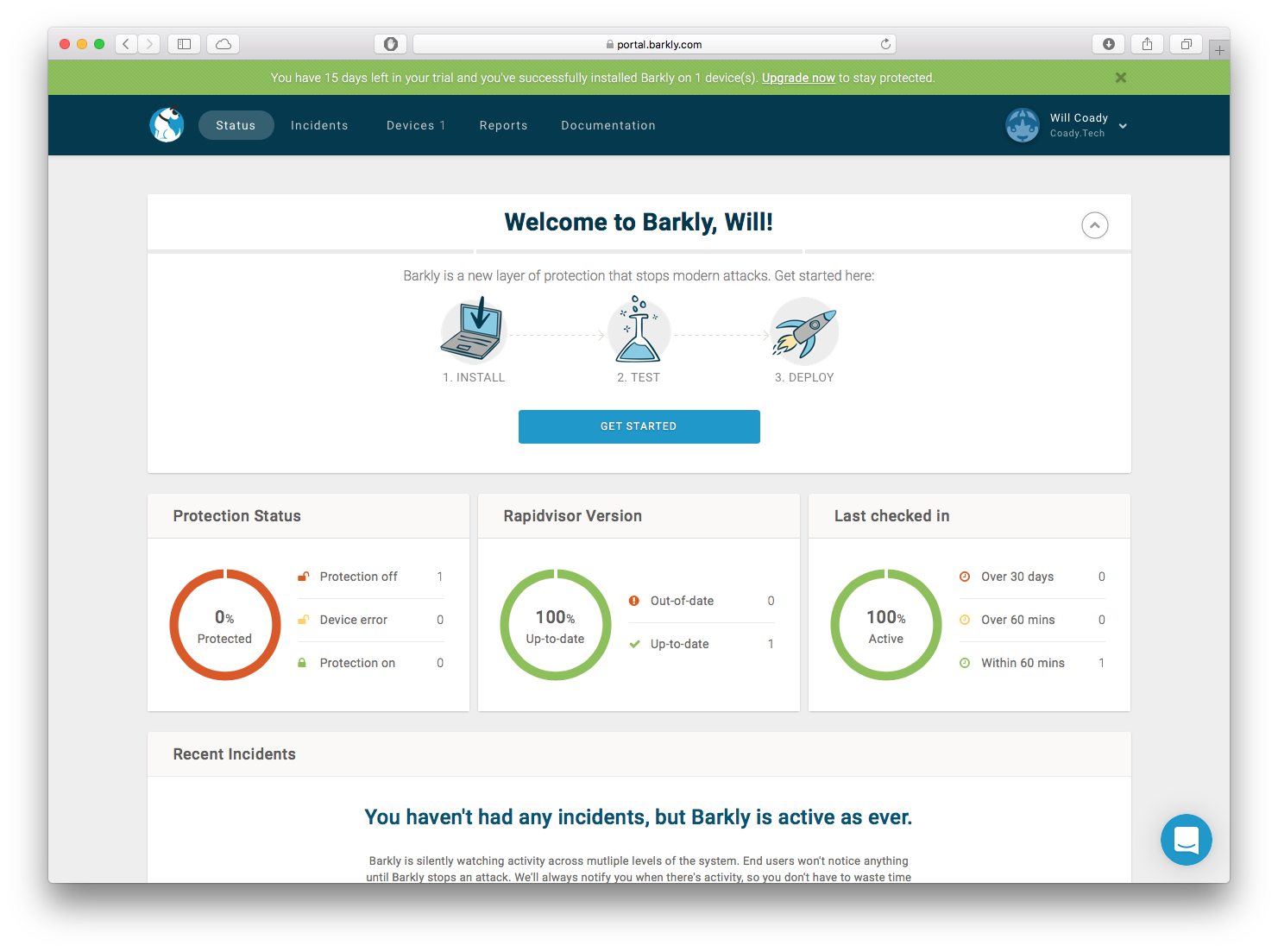
The Barkly Portal ‘getting started’ page
Clicking ‘get started’ downloads a 60MB .exe file ready to install Barkly. The install process is slightly unusual in that once the installation is kicked off, it only prompts for UAC permission. Once complete, there is no confirmation prompt, client control panel, or new icon in the system tray. Instead Barkly sits in the background running silently.
The only mention of Barkly is within Programs and Features of the Windows Control Panel.
Note: It’s worth noting here that as Barkly employs its own Hypervisor, the system must have VT-x extensions turned on and enabled. This shouldn’t be a problem on any computer purchased within the last few years.
Unfortunately for my testing purposes, Hyper-V’s nested virtualisation isn’t supported and so for this review I am making use of VMware’s ESXi 6.5 with nested virtualisation turned on within each VM’s settings.
For larger organisations, Barkly also supports deployment via tools such as Microsoft’s SCCM and group policy. A useable .msi file can be extracted from the .exe installer to provide hands free installation. For those interested, Barkly has a fantastic article on the ins and outs here.
At the present time, Barkly supports both Windows 7 and Windows 10 computers, which should cover the vast majority of Windows OS deployments.
With regards to system performance, I found that the Rapidvisor service had a minimal system footprint.

Resource usage of the Barkly Rapidvisor
Management
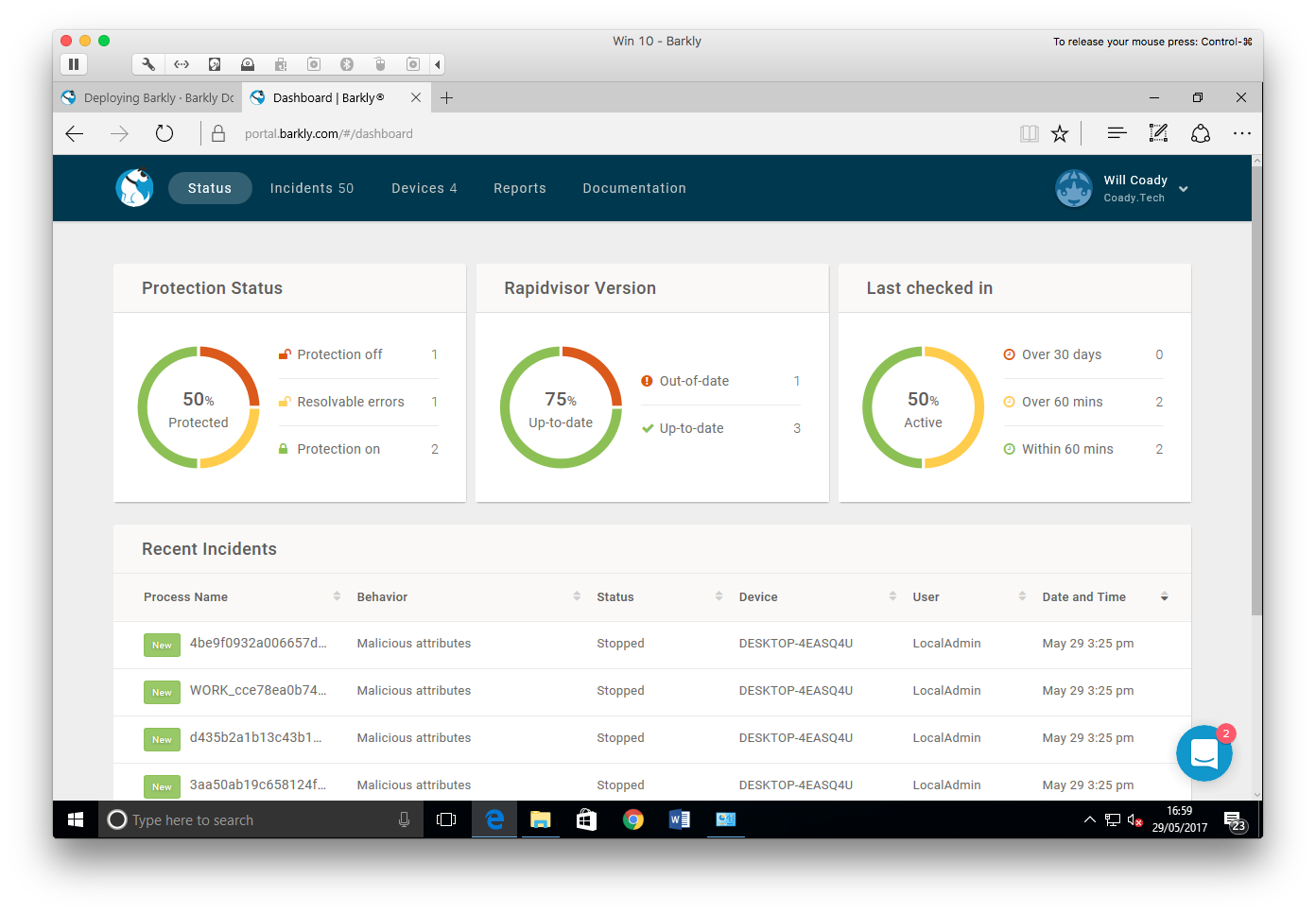
The management console first opens to the status page which provides a general overview on the health of all protected devices, and recent ‘incidents’ (i.e. malware which has been detected and prevented from running).
Rather unique to Barkly, is the instant messenger style chat support built right into the management console. On every page, there is an icon in the bottom right-hand corner which connects straight to support.
If you have any questions, you can have them answered there and then without needing to raise a support ticket. I really liked this feature, and throughout my trial of Barkly, found the support to be superb.
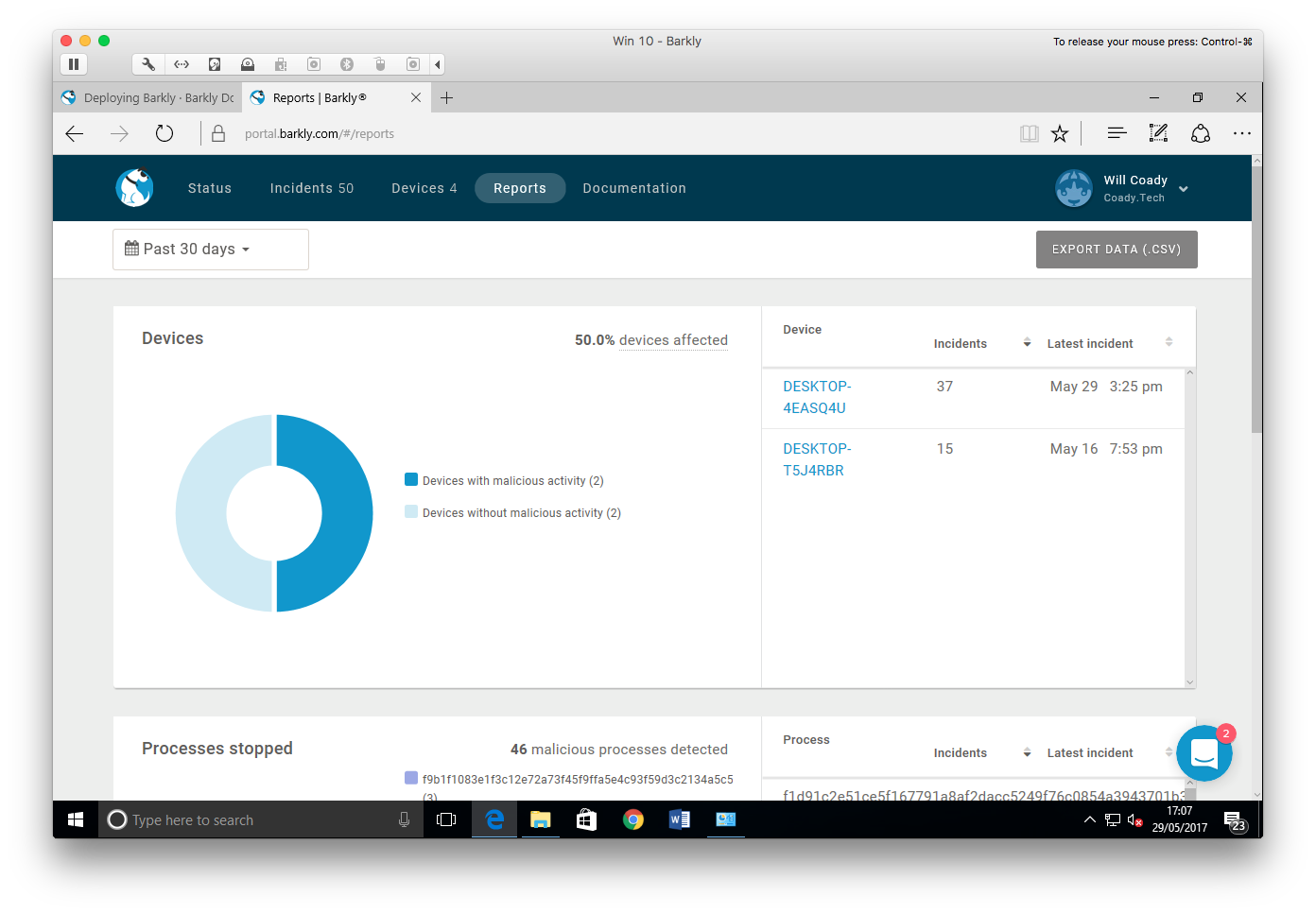
Within the console are four main tabs: Status, Incidents, Devices and Reports.
Starting with the incidents page, we can see some of the threats Barkly blocked during my testing.
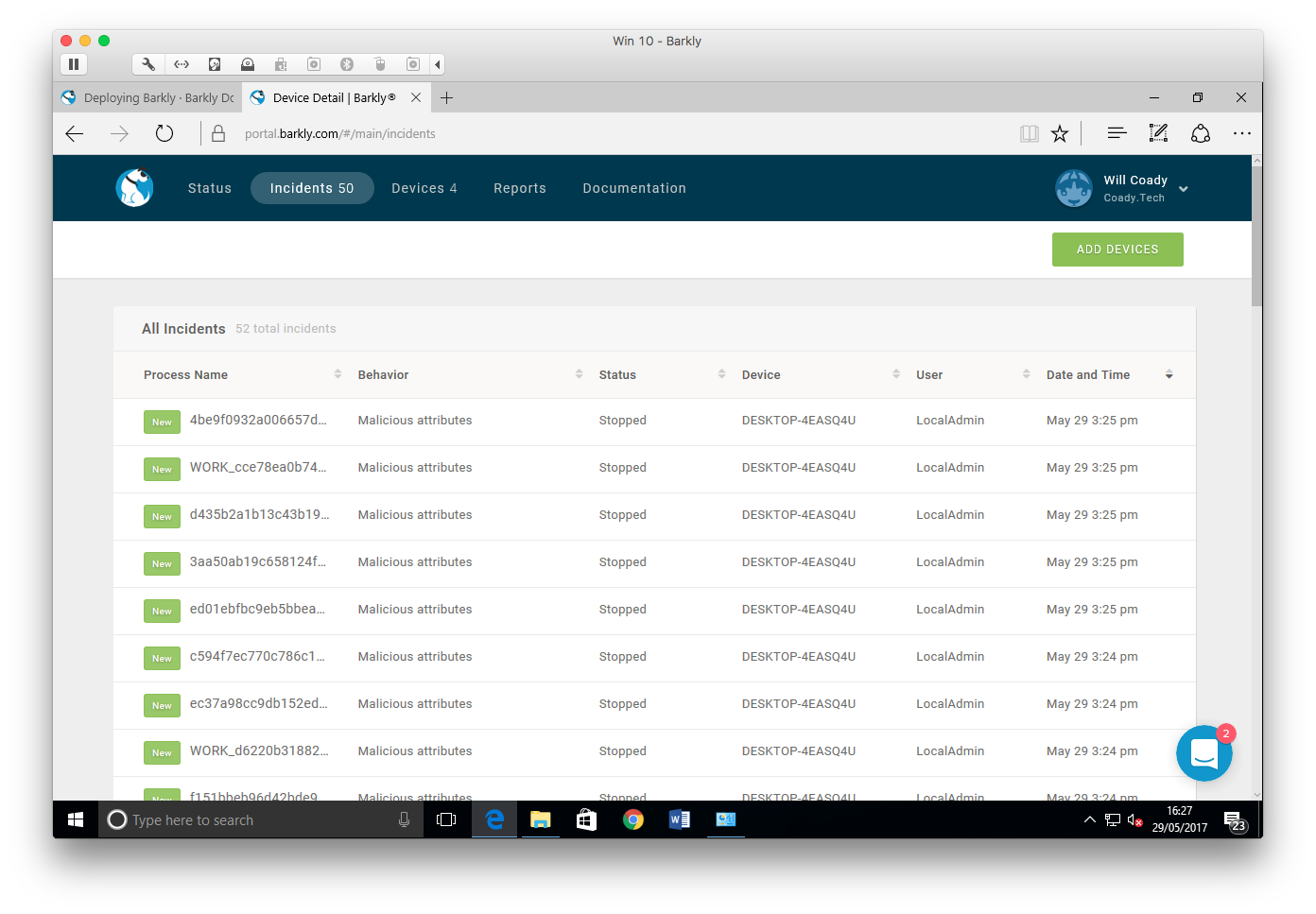
Next up, we have the devices screen. Here a list is shown of all known Barkly protected workstations and their current status.
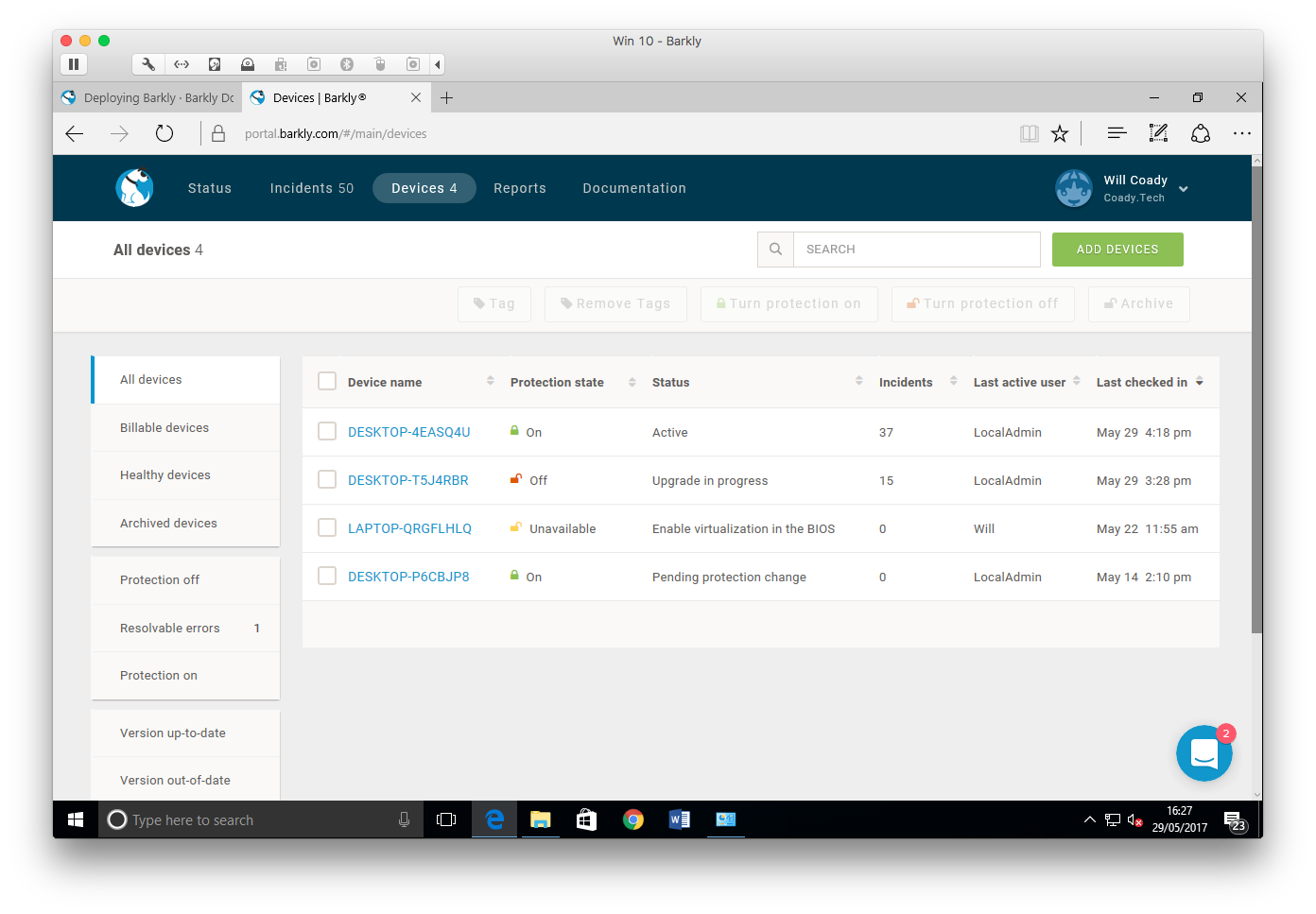
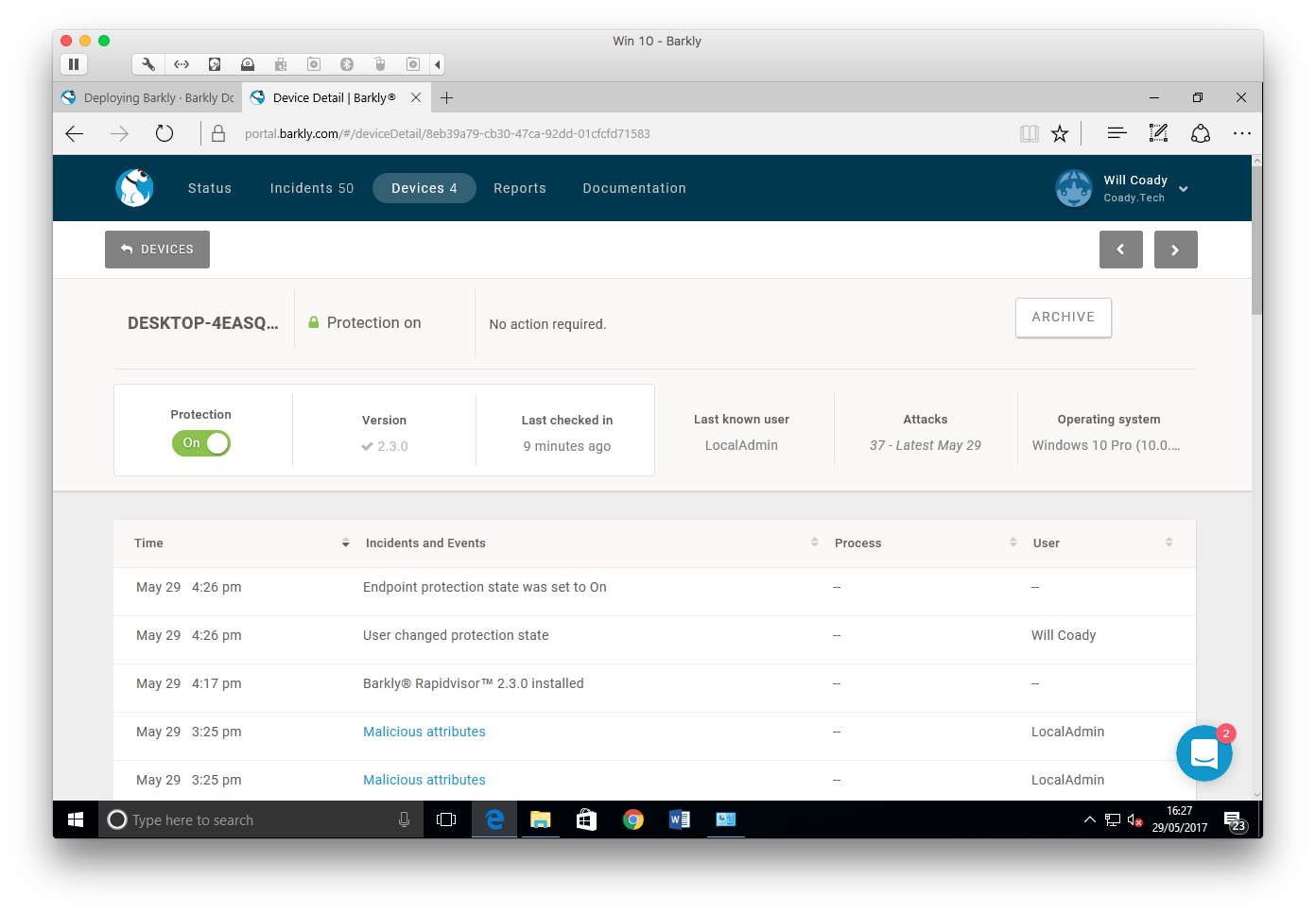
Clicking on a device name brings up further details, allowing protection to be turned on or off, showing recent events and detailing system information such as OS version.
Finally, the reports page pulls together the details from all devices and users, and allows the generation of graphic charts and exportable data to show common processes stopped, users most affected and devices with malicious activity detected.
Testing Methodology
As Barkly recommend running their protection alongside a traditional antivirus, I’m going to be using Microsoft’s built-in Windows Defender on Windows 10 (build 14393).
Stage 1 – Current Malware
- Create a ‘fresh’ Windows 10 virtual machine, install all updates, and install Barkly.
- Create a VMware snapshot.
- Drop malware onto the machine’s desktop.
- Let AV scan the malware, and execute any leftovers.
Stage 2 – New ‘0 day’ Malware
- Revert back to the VMware snapshot.
- Disconnect the VM from the internet and wait three days.
- Introduce malware three days newer than the AV’s signatures.
- Execute all malware.
Stage 3 – Exploits and fileless malware
- Setup a fresh Windows 7 VM with a known vulnerability present (in this case MS17-010)
- Install Barkly
- Attempt to exploit the machine
For this round of testing I’m going to be mashing it up and using a mixture of malware samples from TestMyAV.com, Payload Security, DAS MALWERK, malwr.com, and a manually sourced sample of the WannaCry malware.
To finish off, I’ll also be testing the VM against fileless exploits by utilising the recently leaked FuzzBunch toolkit in an attempt to exploit an SMB vulnerability which has been left purposefully un-patched on my machine.
Stage 1 – Current Malware
Much to my surprise, Windows Defender did very well in this test. After extracting my archive of malware almost everything was detected. Of what remained, the files would either fail to execute, or they would be quarantined by Windows Defender upon opening.
Here you can see the items being quarantined by Defender:

Malware detected by Windows Defender
By the time I had obtained these malware samples, they were already a few hours old. Evidently the malware had already been examined by Microsoft and blacklisted, and as my VM was online and had the latest signature files, the files were blocked.
Unfortunately, due to the effectiveness of Windows Defender, Barkly didn’t get a time to shine during this test. I decided to head straight on to step 2 and see just how well Windows Defender worked with malware which wasn’t in its signature database.
Stage 2 – New or ‘0 day’ malware
Three days later I returned, put together a new mix of malware, and dropped it onto my VM which hadn’t seen the internet since my previous testing.
Straight away, Windows Defender started highlighting threats and quarantining files.
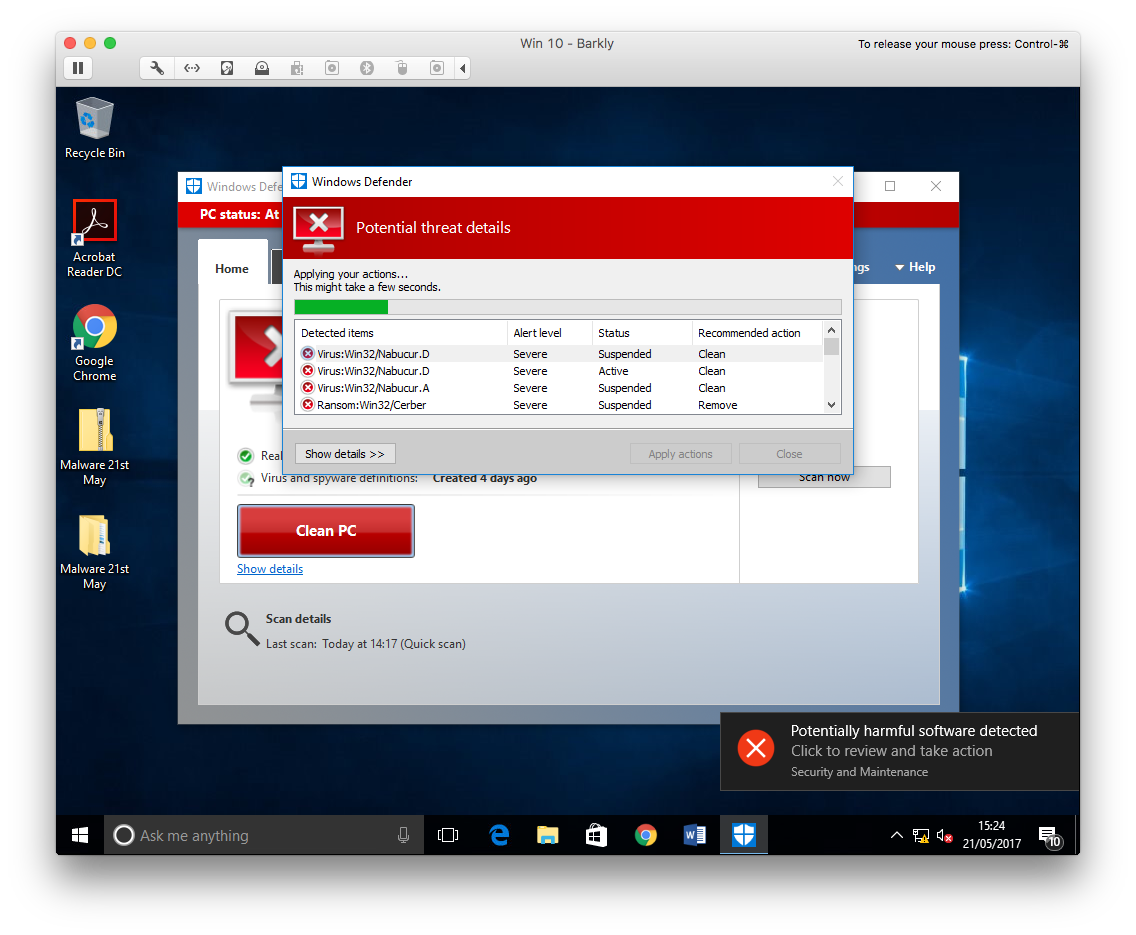
Windows Defender quarantining files
This time though, not everything was removed. In fact quite a few files remained.
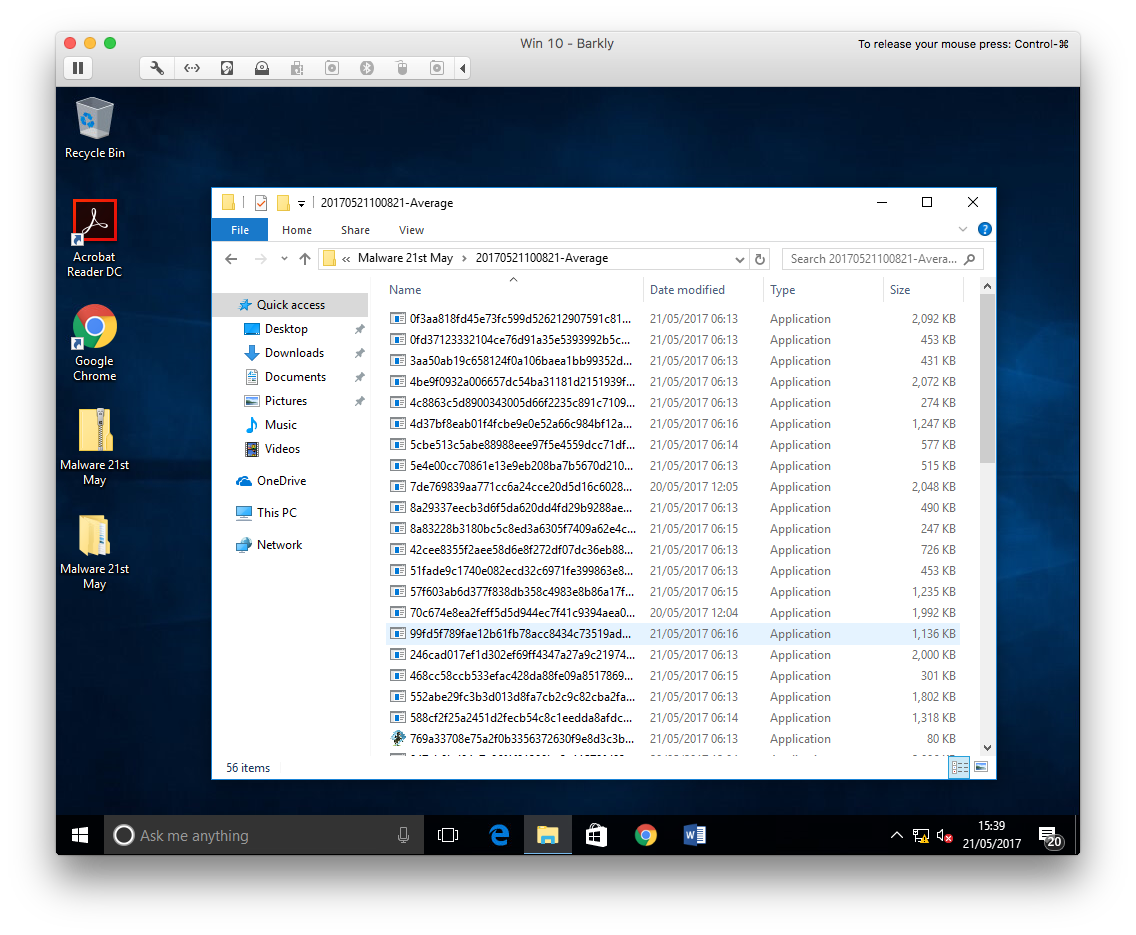
Malware samples missed by Windows Defender
In the above screenshot you can see the set of samples provided by TestMyAV.com. I started here first, executing the files that Windows Defender had left behind one-by-one.
The first couple of files failed to run, showing only a generic Windows error message. By the time I did find a working sample, it seemed to launch but then completely dissapear
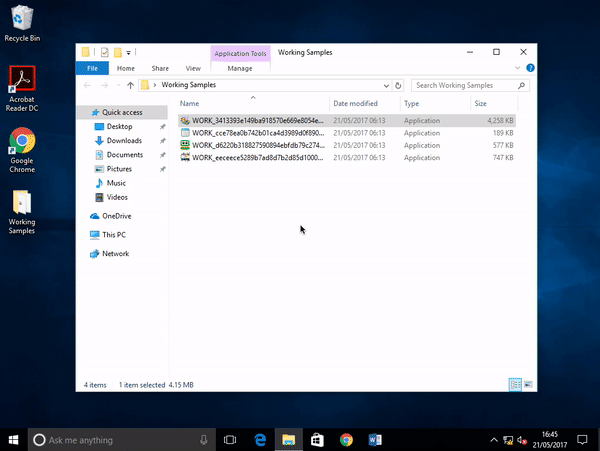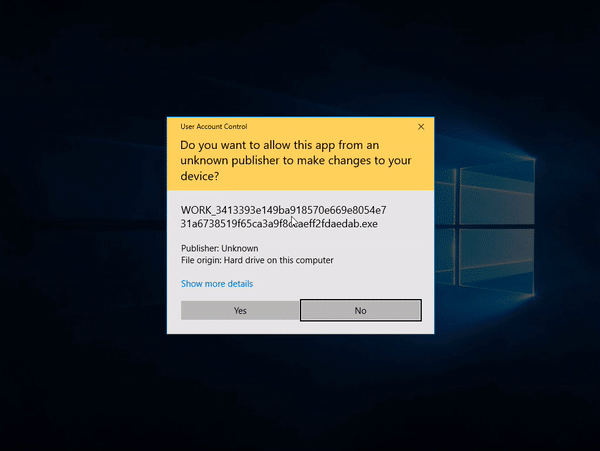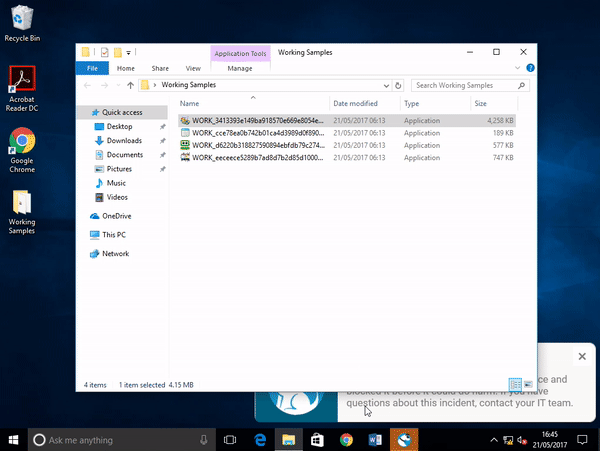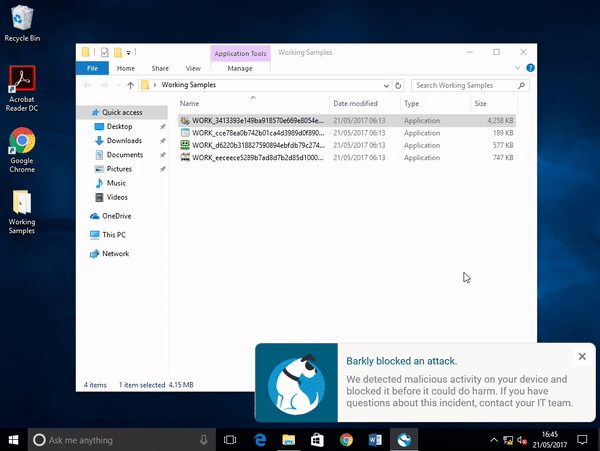
I was starting to think the sample was a dud, but then… Barkly saves the day!
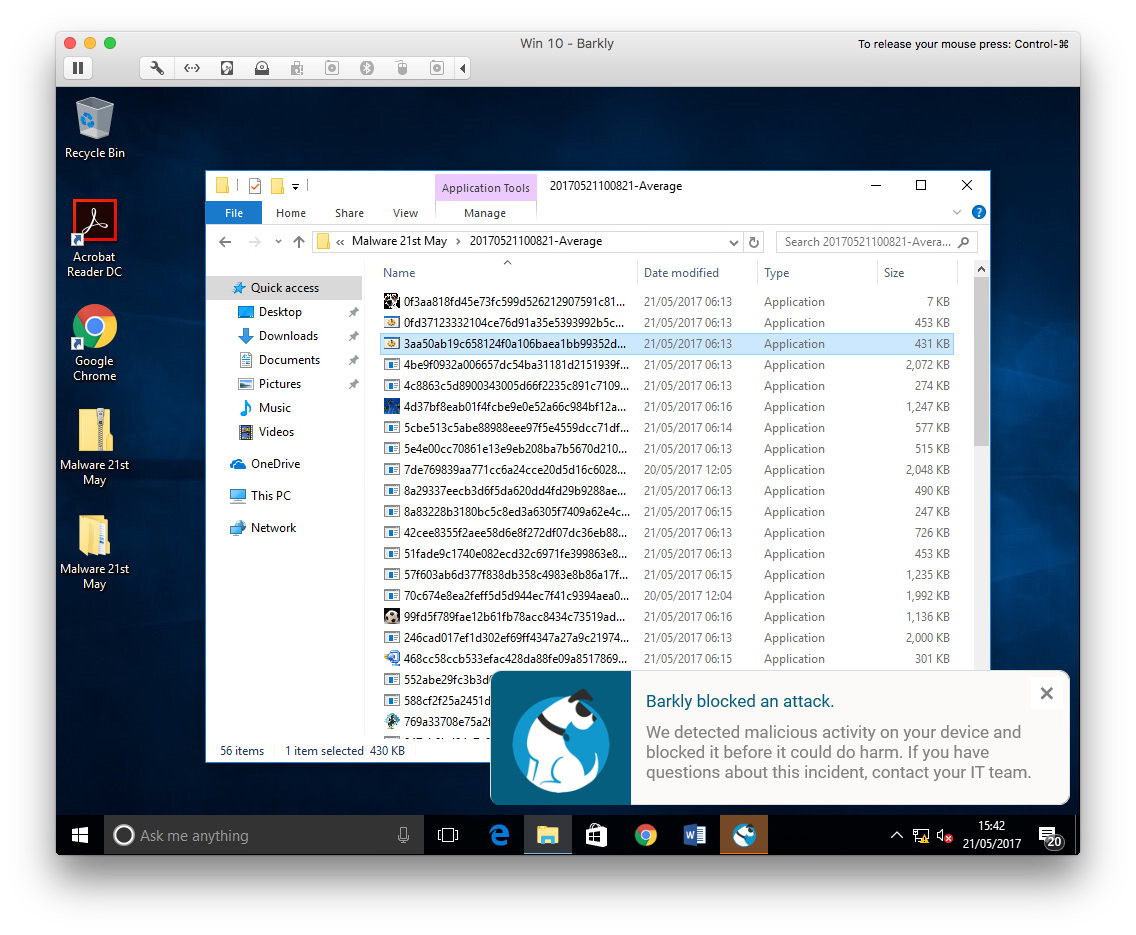
Barkly blocks a threat at runtime
Windows Defender marked the file as safe and had allowed it to run as there was no signatures for it within the Defender definition file (3 days old). Barkly however, managed to detect the behaviour of the file as malicious and terminated it at runtime.
In this video we can see how Barkly behaves when malware is detected.
I continued my testing on each sample, until unfortunately, Barkly faltered.
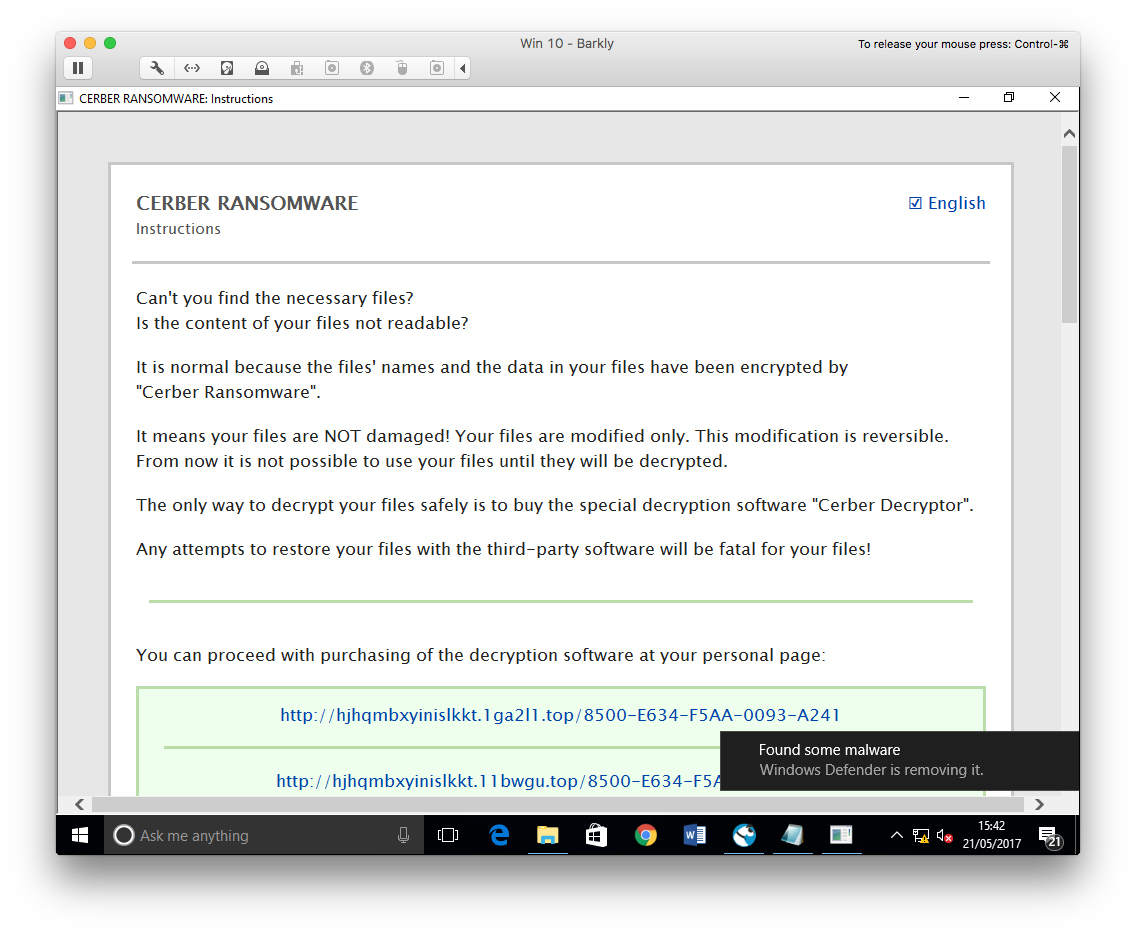
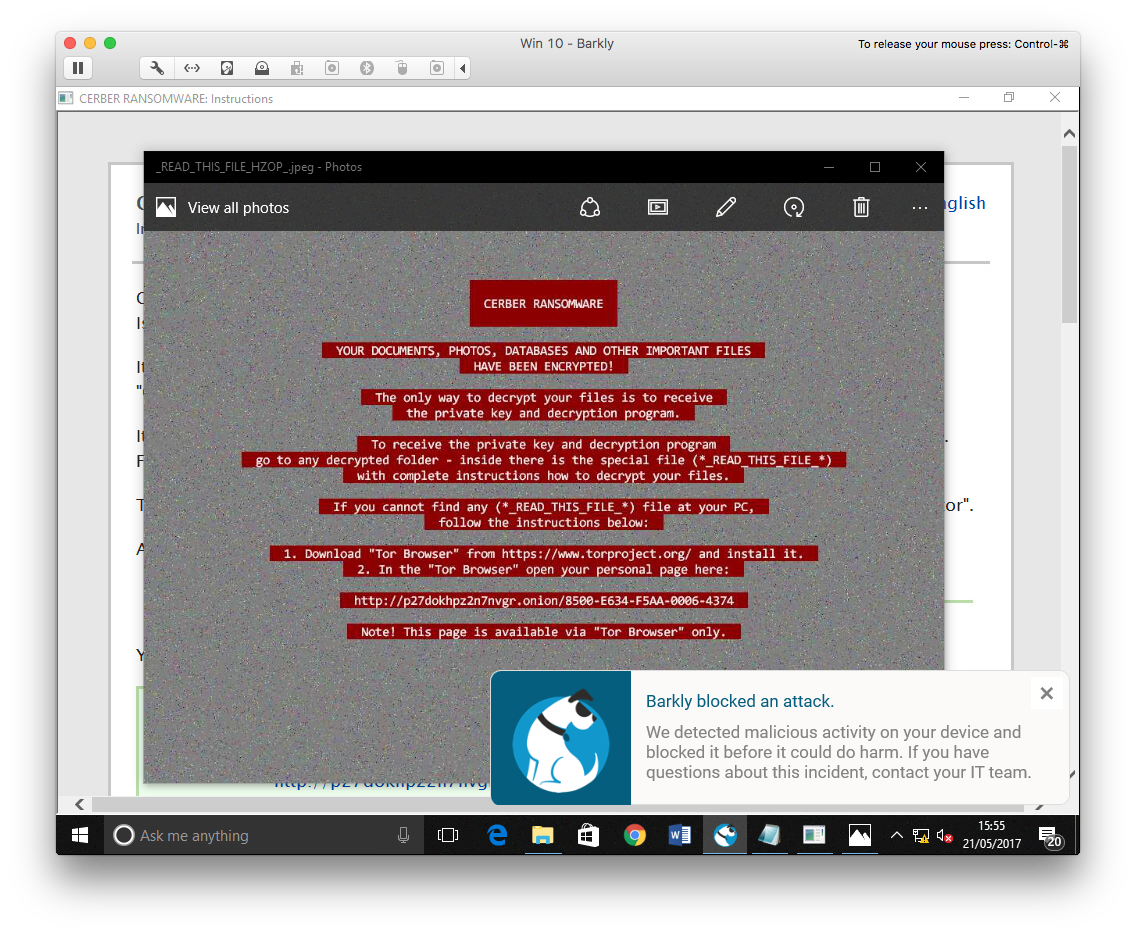
Cerber Ransomware running on a Barkly protected machine
The files on the VM had been encrypted and were no longer accessible. Barkly had allowed ransomware to run on the machine.
Having said that, I feel that Barkly put a strong performance in this area. For a product operating without signatures and at runtime alone, the vast majority of samples were blocked. These were samples which had been marked as clean by Windows Defender.
Results:
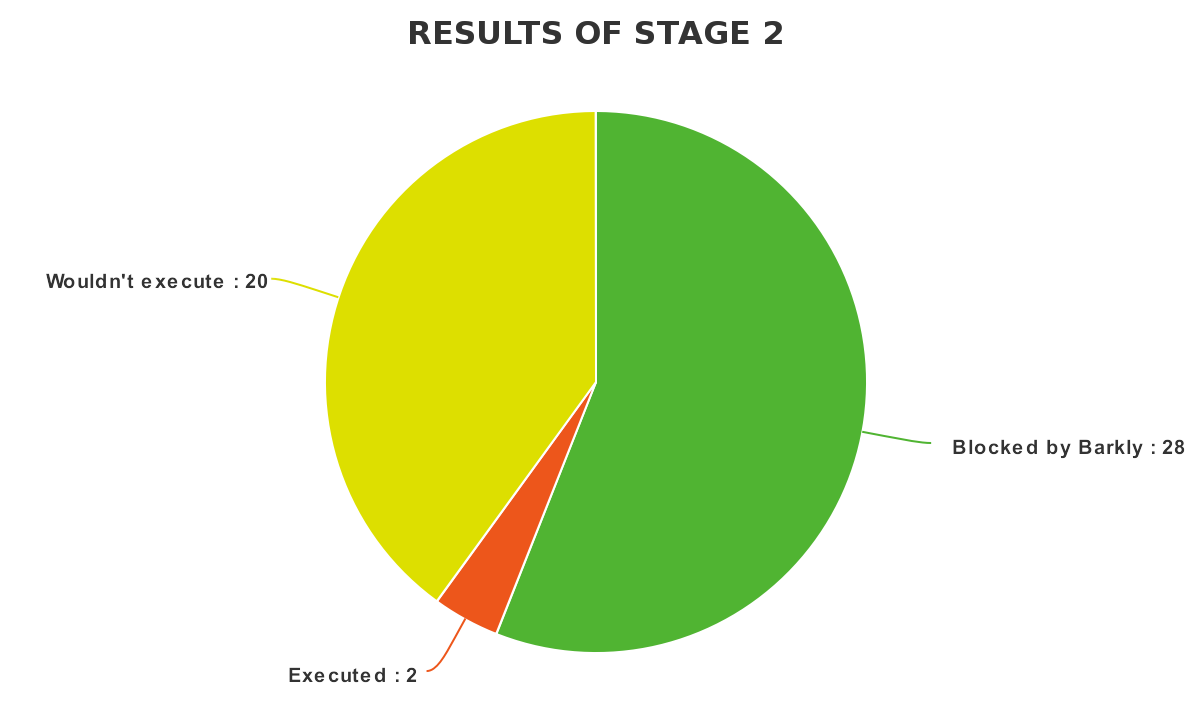
Total malware samples left after a Windows Defender scan: 50
Samples which wouldn’t execute: 20
Samples Blocked by Barkly: 28
Samples Executed: 2
Stage 3 – Exploits and fileless malware
For this stage I’m going to be a little unorthodox and employ some recently leaked hacking tools. They will be used against a Windows 7 target machine, firstly one without any protection, and then against a machine with Barkly installed.
The leaked tools are publicly available here. I will posting an in-depth look at these exploits in a later blog post so stay tuned!
To start, I set myself up a Windows 7 SP1 virtual machine without any security updates installed.
A fresh Windows 7 Enterprise installation without any security updates installed.
In order to make sure the toolkit worked correctly before putting Barkly to the test, I opened Fuzzbunch on my attacker machine and ran the Eternalblue (MS70-010) exploit against the Windows 7 machine.
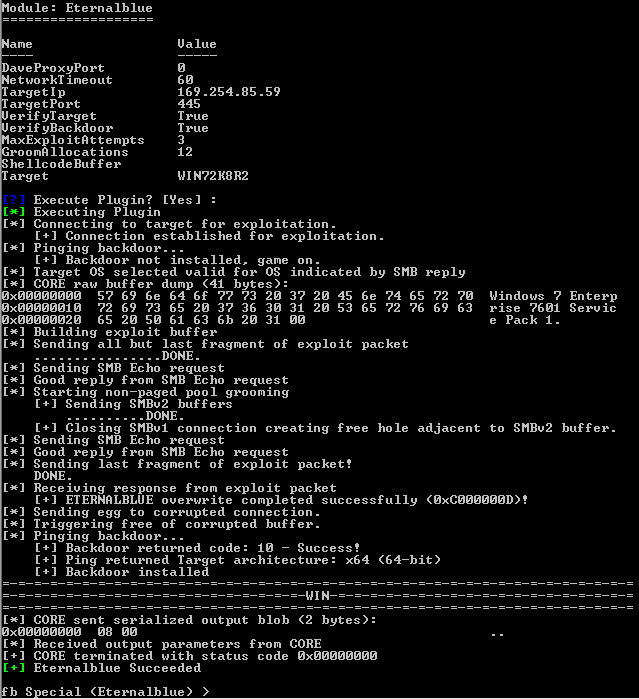
Testing the Eternalblue exploit against a vulnerable machine
As you can see from the above screenshot, the exploit executed perfectly. Just to make sure all was in order, I switched over to the Doublepulsar module and pinged the now embedded backdoor.
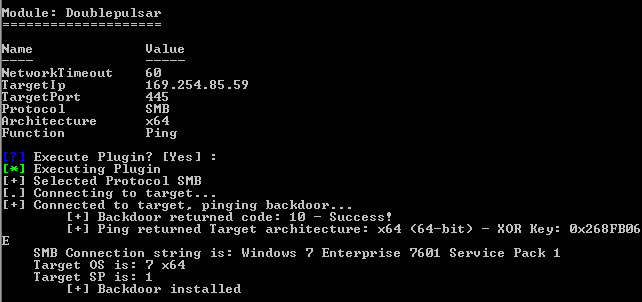
Pinging the backdoor left by Internalblue
The backdoor responded, meaning that the machine was now totally compromised. From here I could load any malicious DLL into runtime memory with SYSTEM level privileges.
I’ll be diving into how these tools work in an up and coming blog post. Stay tuned!
Next up, it was time to test Barkly. I rebooted the VM, installed Barkly, and got ready to test again.
Just as I had done so before, I ran the Eternalblue exploit against the now Barkly protected machine.
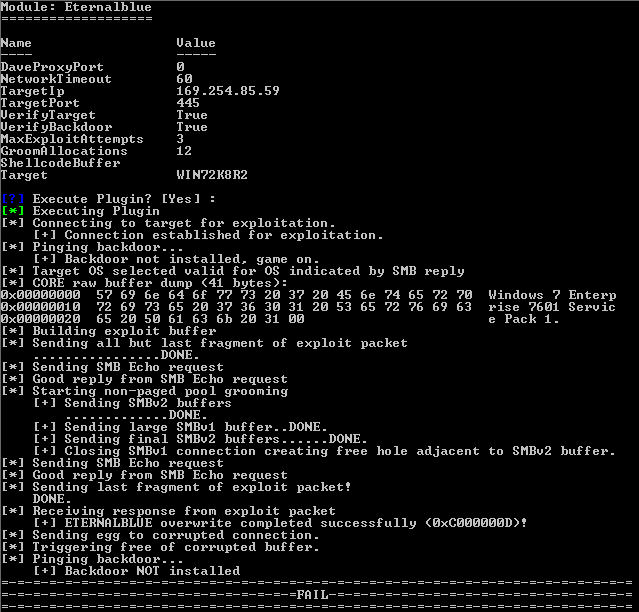
Eternalblue exploit fails against a Barkly protected machine
Eternalblue exploit fails against a Barkly protected machine.
Success! The exploit failed to execute. Rather interestingly, Barkly didn’t report this blocking action to the user, but none the less, my machine had been protected.
Closing Thoughts
Barkly is a rather unique product, not attempting to compete with antivirus, but instead trying to compliment it in such a way so as to improve resiliency against new and unknown threats.
The Rapidvisor had absolute minimal impact on systems resources, only consuming on average 7MB of system memory and never once noticeably slowing the machine down. Users are never bothered or prompted by the software unless a threat is detected and stopped.
As can be seen from the testing results, Antivirus can and does perform well against known threats when kept up to date with the latest signature files. So well, in fact, that Barkly wasn’t even needed in stage 1 of testing.
However, as soon as malware unknown to the antivirus was introduced, it was a different story. Here we saw Barkly put to the test, blocking 28 out of 30 threats, equating to a 93% block rate. Barkly also managed to detect and prevent an entirely in-memory (fileless) exploit.
Although not a perfect score, I do feel that Barkly has proven itself to be a valuable product. Operating on behavioural analysis alone, it detected all but two unknown threats.
In the future I hope Barkly will continue to work on the Rapidvisor to offer even better levels of protection. My only real criticism is a lack of support for Microsoft’s Hyper-V. With security features such as Windows 10’s credential guard requiring Hyper-V, it would be a shame to rule out Barkly from these environments.
Overall verdict: 4.5/5
Comments