Resolving the AWS Amplify Certificate Authority Authentication error

I recently moved this very website over to AWS Amplify, away from the traditional VPS and WordPress approach. Whilst everything worked fine in development, trying to add my domain name registered with CloudFlare to AWS Amplify’s domain manager returned a Certificate Authority Authentication error.
In this post I’ll detail the problem and how to go about fixing it..
1 The problem
If you have a domain using CloudFlare name servers for DNS and try to register it with Amazon’s Amplify service you may receive the following error message:
“Error message: The status of this certificate request is “Failed”. One or more domain names have failed validation due to a Certificate Authority Authentication error. Learn more…”
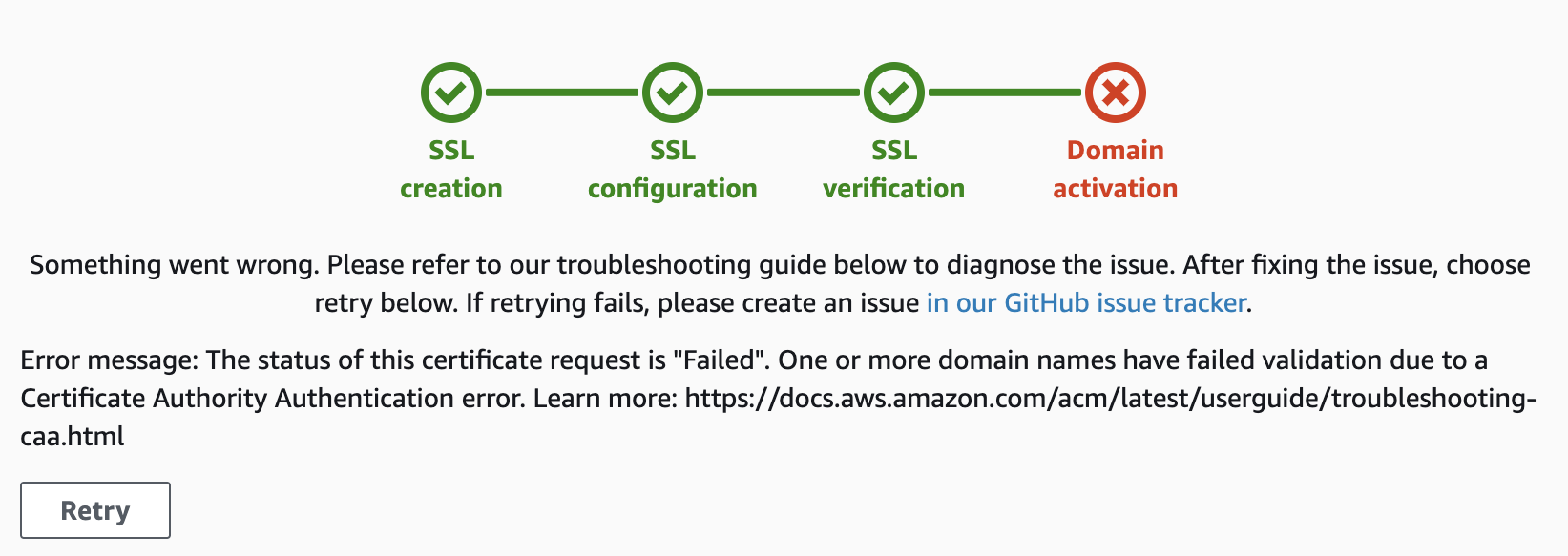
AWS Amplify CAA Error
2 Why this happens
I believe the problem comes about when using CloudFlare’s Universal SSL feature. Behind the scenes CloudFlare quietly creates a number of DNS CAA records which aren’t visible within the DNS management portal.
Running the ‘dig’ command returned the following results for my domain (this website) Coady.Tech.
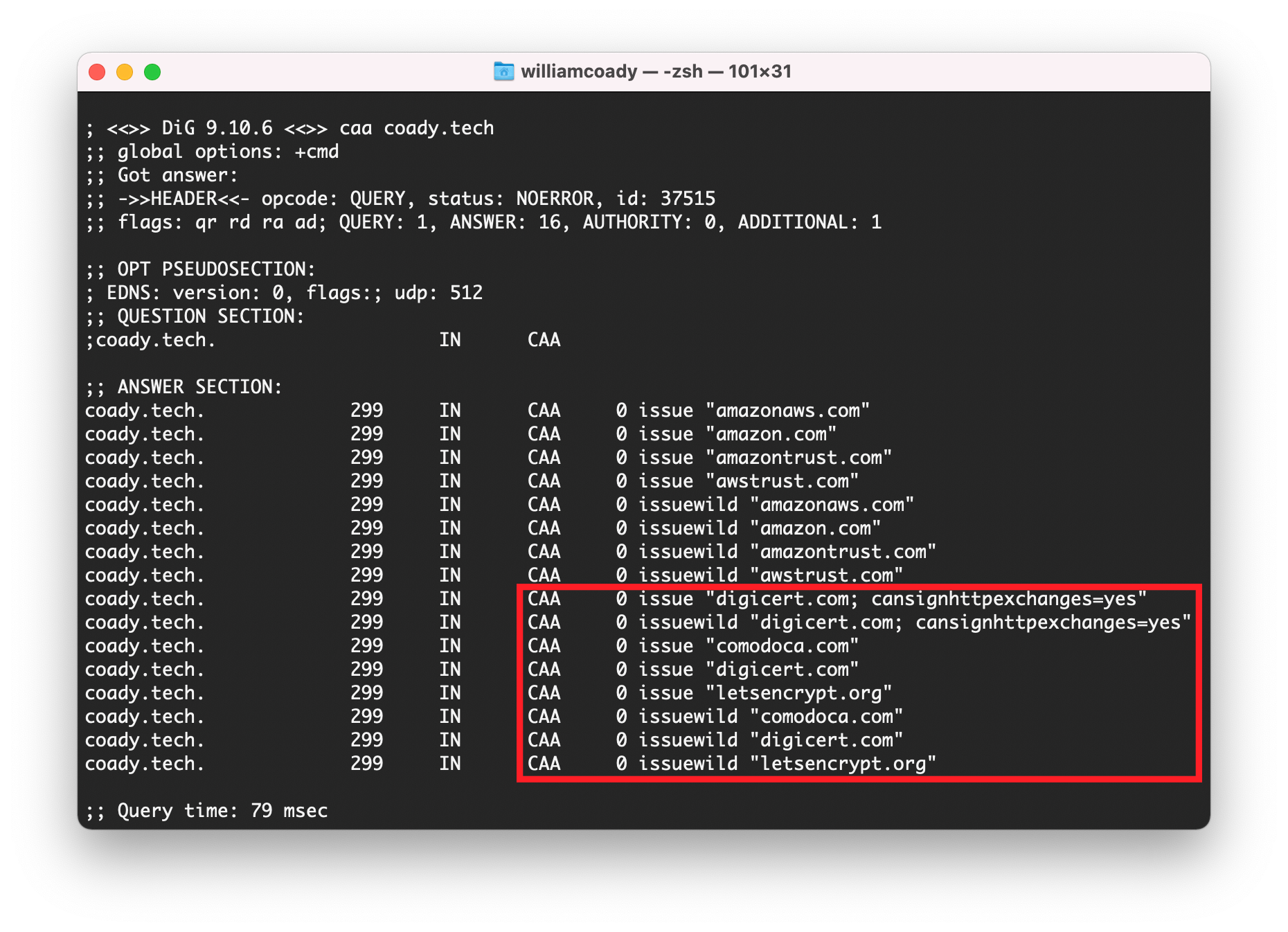
DiG Output shows CAA records
CAA records, also knows as Certification Authority Authorization records, are used to restrict which Certificate Authorities are allowed to issue certificates for your domain. In this instance it seems CloudFlare’s Universal SSL automatically created CAA records for the providers they use, including Let’s Encrypt, DigiCert, and others.
When AWS Amplify attempts to issue you with a certificate their system will check your domain’s CAA records. If AWS isn’t listed then it will return an error.
3 Solution
The solution is to create root and wildcard CAA records to authorize AWS to issue certificates for your domain.
Within the CloudFlare DNS manager select Add record and create a record for each domain name with the following options:
- Record type as CAA
- Name as @
- TTL as Auto
- Tag as Only allow specific hostnames
Repeat this for each AWS domain name:
- amazonaws.com
- amazon.com
- amazontrust.com
- awstrust.com
Once complete, repeat the above process four more times but with the tag field changed to Only allow wildcards.
You should end up with four issue CAA records and another four issuewild wildcard CAA records as shown in the example below:
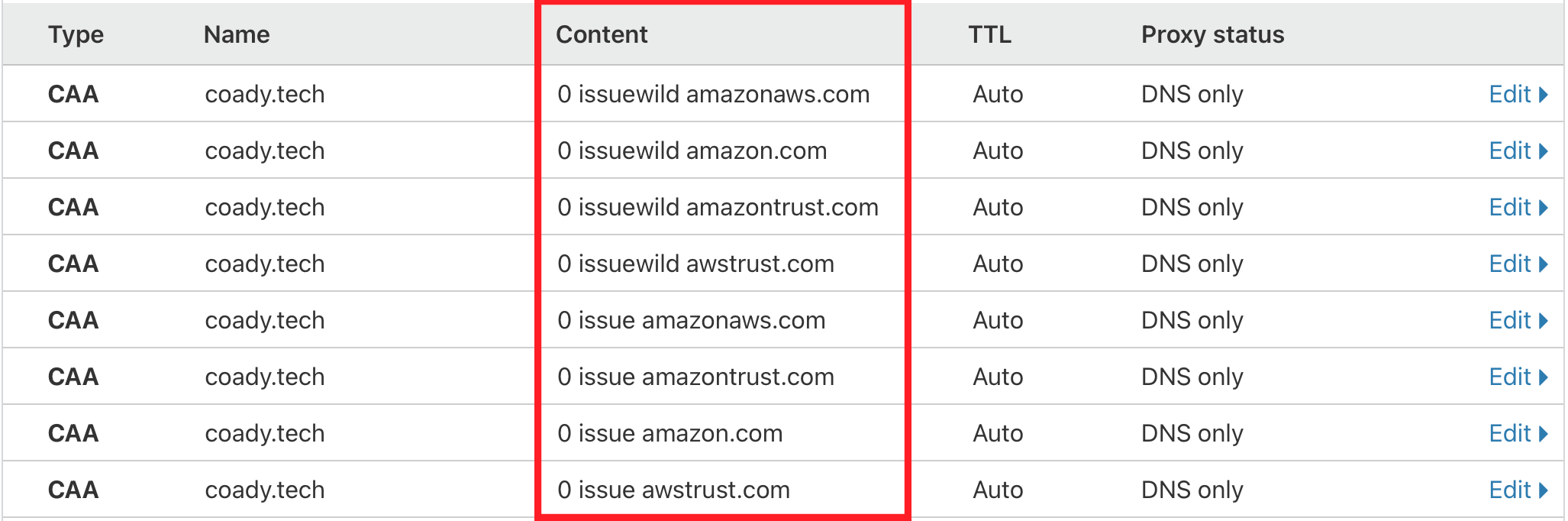
Four 'issue', and four 'issuewild' CAA records
4 Summary
That’s it!
If you have any questions please drop me a message in the comments section below.
Comments